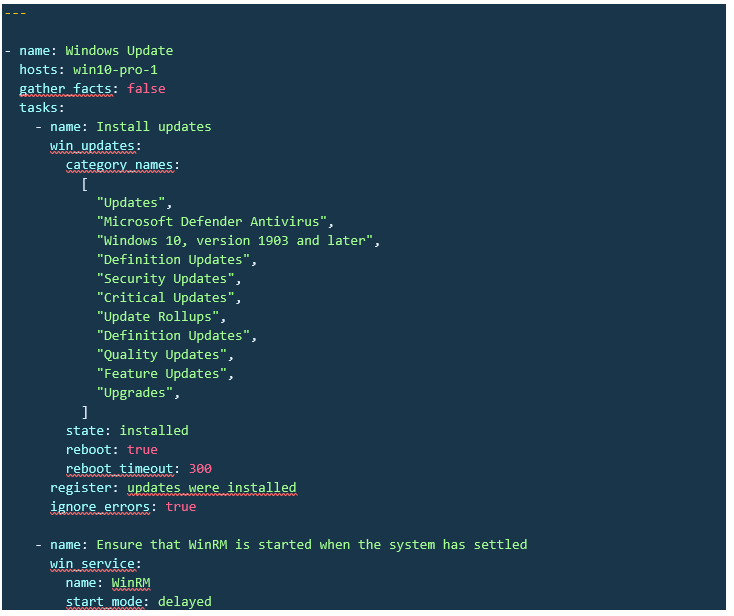
I was not able to attache a text file so here is the contents of them. The first one ins what I ran before trying to install any updates. The second file is what I get after trying to install the updates:
First File:
2020-07-27 09:20:56Z WUA is available in current logon process, running natively
2020-07-27 09:20:56Z Creating Windows Update session…
2020-07-27 09:20:56Z Create Windows Update searcher…
2020-07-27 09:20:56Z Setting the Windows Update Agent source catalog…
2020-07-27 09:20:56Z Requested search source is ‘default’
2020-07-27 09:20:56Z Search source set to ‘default’ (ServerSelection = 0)
2020-07-27 09:20:56Z Searching for updates to install
2020-07-27 09:21:11Z Found 11 updates
2020-07-27 09:21:11Z Creating update collection…
2020-07-27 09:21:11Z Adding update 3b80c9f0-1416-4f38-bc39-e68ec91b71fa - Update for Adobe Flash Player for Windows 10 Version 1809 for x64-based Systems (KB4462930)
2020-07-27 09:21:11Z Adding update b885d48a-be89-4b3b-9e02-66896c88b568 - Microsoft .NET Framework 4.8 for Windows 10 Version 1809 for x64 (KB4486153)
2020-07-27 09:21:11Z Adding update 62afbd9b-097b-4300-9e4d-275c9a35be2c - Update for Windows Defender Antivirus antimalware platform - KB4052623 (Version 4.18.2001.10)
2020-07-27 09:21:11Z Adding update 2221dd34-39bb-4f16-b320-be49fe4a6b95 - Windows Malicious Software Removal Tool x64 - v5.82 (KB890830)
2020-07-27 09:21:11Z Adding update d7788cdf-043f-4920-a066-d5aa76366ce5 - 2020-01 Update for Windows 10 Version 1809 for x64-based Systems (KB4494174)
2020-07-27 09:21:11Z Adding update f0373bed-690d-454b-898d-e5a20a4e4f90 - 2020-06 Security Update for Adobe Flash Player for Windows 10 Version 1809 for x64-based Systems (KB4561600)
2020-07-27 09:21:11Z Adding update 574c4e34-7a64-4d62-a90d-62818c403ae0 - Update for Microsoft Defender Antivirus antimalware platform - KB4052623 (Version 4.18.2006.10)
2020-07-27 09:21:11Z Adding update 9add809d-6ff7-41cc-b891-2fe92d2aa759 - 2020-07 Cumulative Update Preview for .NET Framework 3.5, 4.7.2 and 4.8 for Windows 10 Version 1809 for x64 (KB4567327)
2020-07-27 09:21:11Z Adding update b189e214-800b-46f6-8d32-fae39d1ec62a - Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (Version 1.319.2408.0)
2020-07-27 09:21:11Z Adding update 75be4a80-6464-4d06-b0b7-fdc57c1762bf - 2019-12 Update for Windows 10 Version 1809 for x64-based Systems (KB4023057)
2020-07-27 09:21:11Z Adding update ac2b20ab-6186-4267-8d55-4b3ca35197d1 - Feature update to Windows 10, version 1909
2020-07-27 09:21:11Z Calculating pre-install reboot requirement…
2020-07-27 09:21:11Z Check mode: exiting…
2020-07-27 09:21:11Z Return value:
{
“updates”: {
“2221dd34-39bb-4f16-b320-be49fe4a6b95”: {
“categories”: [
“Update Rollups”,
“Windows 10”,
“Windows 10 LTSB”
],
“title”: “Windows Malicious Software Removal Tool x64 - v5.82 (KB890830)”,
“id”: “2221dd34-39bb-4f16-b320-be49fe4a6b95”,
“installed”: false,
“kb”: [
“890830”
]
},
“62afbd9b-097b-4300-9e4d-275c9a35be2c”: {
“categories”: [
“Microsoft Defender Antivirus”,
“Updates”
],
“title”: “Update for Windows Defender Antivirus antimalware platform - KB4052623 (Version 4.18.2001.10)”,
“id”: “62afbd9b-097b-4300-9e4d-275c9a35be2c”,
“installed”: false,
“kb”: [
“4052623”
]
},
“9add809d-6ff7-41cc-b891-2fe92d2aa759”: {
“categories”: [
“Updates”,
“Windows 10”,
“Windows 10 LTSB”
],
“title”: “2020-07 Cumulative Update Preview for .NET Framework 3.5, 4.7.2 and 4.8 for Windows 10 Version 1809 for x64 (KB4567327)”,
“id”: “9add809d-6ff7-41cc-b891-2fe92d2aa759”,
“installed”: false,
“kb”: [
“4567327”
]
},
“d7788cdf-043f-4920-a066-d5aa76366ce5”: {
“categories”: [
“Updates”,
“Windows 10”
],
“title”: “2020-01 Update for Windows 10 Version 1809 for x64-based Systems (KB4494174)”,
“id”: “d7788cdf-043f-4920-a066-d5aa76366ce5”,
“installed”: false,
“kb”: [
“4494174”
]
},
“b189e214-800b-46f6-8d32-fae39d1ec62a”: {
“categories”: [
“Definition Updates”,
“Microsoft Defender Antivirus”
],
“title”: “Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (Version 1.319.2408.0)”,
“id”: “b189e214-800b-46f6-8d32-fae39d1ec62a”,
“installed”: false,
“kb”: [
“2267602”
]
},
“75be4a80-6464-4d06-b0b7-fdc57c1762bf”: {
“categories”: [
“Critical Updates”
],
“title”: “2019-12 Update for Windows 10 Version 1809 for x64-based Systems (KB4023057)”,
“id”: “75be4a80-6464-4d06-b0b7-fdc57c1762bf”,
“installed”: false,
“kb”: [
“4023057”
]
},
“574c4e34-7a64-4d62-a90d-62818c403ae0”: {
“categories”: [
“Definition Updates”,
“Microsoft Defender Antivirus”
],
“title”: “Update for Microsoft Defender Antivirus antimalware platform - KB4052623 (Version 4.18.2006.10)”,
“id”: “574c4e34-7a64-4d62-a90d-62818c403ae0”,
“installed”: false,
“kb”: [
“4052623”
]
},
“f0373bed-690d-454b-898d-e5a20a4e4f90”: {
“categories”: [
“Security Updates”,
“Windows 10”,
“Windows 10 LTSB”
],
“title”: “2020-06 Security Update for Adobe Flash Player for Windows 10 Version 1809 for x64-based Systems (KB4561600)”,
“id”: “f0373bed-690d-454b-898d-e5a20a4e4f90”,
“installed”: false,
“kb”: [
“4561600”
]
},
“b885d48a-be89-4b3b-9e02-66896c88b568”: {
“categories”: [
“Feature Packs”,
“Windows 10”
],
“title”: “Microsoft .NET Framework 4.8 for Windows 10 Version 1809 for x64 (KB4486153)”,
“id”: “b885d48a-be89-4b3b-9e02-66896c88b568”,
“installed”: false,
“kb”: [
“4486153”
]
},
“3b80c9f0-1416-4f38-bc39-e68ec91b71fa”: {
“categories”: [
“Updates”,
“Windows 10”
],
“title”: “Update for Adobe Flash Player for Windows 10 Version 1809 for x64-based Systems (KB4462930)”,
“id”: “3b80c9f0-1416-4f38-bc39-e68ec91b71fa”,
“installed”: false,
“kb”: [
“4462930”
]
},
“ac2b20ab-6186-4267-8d55-4b3ca35197d1”: {
“categories”: [
“Upgrades”
],
“title”: “Feature update to Windows 10, version 1909”,
“id”: “ac2b20ab-6186-4267-8d55-4b3ca35197d1”,
“installed”: false,
“kb”: [
“4560960”
]
}
},
“found_update_count”: 11,
“changed”: false,
“reboot_required”: false,
“installed_update_count”: 0,
“filtered_updates”: {
}
}
2020-07-27 09:21:11Z Native job completed with output:
Name Value
updates {2221dd34-39bb-4f16-b320-be49fe4a6b95, 62afbd9b-097b-4300-9e4d-275c9a35be2c, 9add809d-6ff7-41cc-b891-2fe92d2aa759, d7788cdf-043f-4920-a066-d5aa76366ce5…}
found_update_count 11
changed False
reboot_required False
installed_update_count 0
filtered_updates {}
Second file:
2020-07-27 11:09:37Z WUA is available in current logon process, running natively
2020-07-27 11:09:37Z Creating Windows Update session…
2020-07-27 11:09:37Z Create Windows Update searcher…
2020-07-27 11:09:37Z Setting the Windows Update Agent source catalog…
2020-07-27 11:09:37Z Requested search source is ‘default’
2020-07-27 11:09:37Z Search source set to ‘default’ (ServerSelection = 0)
2020-07-27 11:09:37Z Searching for updates to install
2020-07-27 11:09:41Z Found 3 updates
2020-07-27 11:09:41Z Creating update collection…
2020-07-27 11:09:41Z Adding update b885d48a-be89-4b3b-9e02-66896c88b568 - Microsoft .NET Framework 4.8 for Windows 10 Version 1809 for x64 (KB4486153)
2020-07-27 11:09:41Z Adding update 733586b1-2335-40ff-8ff4-86da119d371f - Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (Version 1.319.2413.0)
2020-07-27 11:09:41Z Adding update ac2b20ab-6186-4267-8d55-4b3ca35197d1 - Feature update to Windows 10, version 1909
2020-07-27 11:09:41Z Calculating pre-install reboot requirement…
2020-07-27 11:09:41Z Check mode: exiting…
2020-07-27 11:09:41Z Return value:
{
“updates”: {
“733586b1-2335-40ff-8ff4-86da119d371f”: {
“categories”: [
“Definition Updates”,
“Microsoft Defender Antivirus”
],
“title”: “Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (Version 1.319.2413.0)”,
“id”: “733586b1-2335-40ff-8ff4-86da119d371f”,
“installed”: false,
“kb”: [
“2267602”
]
},
“b885d48a-be89-4b3b-9e02-66896c88b568”: {
“categories”: [
“Feature Packs”,
“Windows 10”
],
“title”: “Microsoft .NET Framework 4.8 for Windows 10 Version 1809 for x64 (KB4486153)”,
“id”: “b885d48a-be89-4b3b-9e02-66896c88b568”,
“installed”: false,
“kb”: [
“4486153”
]
},
“ac2b20ab-6186-4267-8d55-4b3ca35197d1”: {
“categories”: [
“Upgrades”
],
“title”: “Feature update to Windows 10, version 1909”,
“id”: “ac2b20ab-6186-4267-8d55-4b3ca35197d1”,
“installed”: false,
“kb”: [
“4560960”
]
}
},
“found_update_count”: 3,
“changed”: false,
“reboot_required”: true,
“installed_update_count”: 0,
“filtered_updates”: {
}
}
2020-07-27 11:09:42Z Native job completed with output:
Name Value
updates {733586b1-2335-40ff-8ff4-86da119d371f, b885d48a-be89-4b3b-9e02-66896c88b568, ac2b20ab-6186-4267-8d55-4b3ca35197d1}
found_update_count 3
changed False
reboot_required True
installed_update_count 0
filtered_updates {}